Terraform Advanced Topics: workspaces, remote execution, and collaboration features in Terraform.
Table of contents
- TerraWeek Day 7/7
- What are workspaces, remote execution, and collaboration features in Terraform?
- Concept of Terraform workspaces and understand how they can be utilized to manage multiple environments.
- Explore remote execution options such as using remote backends (e.g., AWS S3, Azure Storage Account, or HashiCorp Consul) and understand the benefits they offer.
- Collaboration tools like HashiCorp Terraform Cloud or Terraform Enterprise
- What are the best practices for organizing your Terraform code, version control, and CI/CD integration?
- Features of Terraform Cloud, Terraform Enterprise, and Terraform Registry
TerraWeek Day 7/7
What are workspaces, remote execution, and collaboration features in Terraform?
Concept of Terraform workspaces and understand how they can be utilized to manage multiple environments.
Terraform Workspaces allow you to manage multiple environments independently within a single Terraform configuration. A workspace is a unique state environment that represents a particular environment or configuration. For example, you may have different workspaces for development, staging, and production environments.
Each workspace can contain different settings or variables, such as different credentials, network configurations, or instance types. However, you will typically use the same Terraform configuration code across all workspaces.
Here are some of the key benefits of using Terraform Workspaces:
Organize infrastructure as code for different environments in a single codebase.
Separate state files for each environment, reducing the risk of misconfiguration or conflicts between environments.
Reduce the duplication of code across multiple configurations.
Step-by-step guide on how to use Terraform workspaces:
- Create a new directory for your Terraform configuration and initialize it with the
terraform initcommand.
$ mkdir my-infra
$ cd my-infra
$ terraform init
- Create a new Terraform configuration file (e.g., main.tf) and define the resources for your infrastructure.
# main.tf
provider "aws" {
region = "us-west-1"
}
resource "aws_instance" "example" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
}
- Create a new workspace for the dev environment:
$ terraform workspace new dev
- Switch to the new dev workspace:
$ terraform workspace select dev
- Create a new variable file for the dev environment (e.g., dev.tfvars) and set the variable values specific to this environment.
# dev.tfvars
access_key = "your_access_key_here"
secret_key = "your_secret_key_here"
- Validate that the configuration syntax for the dev workspace is correct:
$ terraform validate -var-file=dev.tfvars
- Apply the Terraform configuration to create resources in the dev environment:
$ terraform apply -var-file=dev.tfvars
- Create a new workspace for the prod environment:
$ terraform workspace new prod
- Switch to the new prod workspace:
$ terraform workspace select prod
- Create a new variable file for the prod environment (e.g., prod.tfvars) and set the variable values specific to this environment.
# prod.tfvars
access_key = "your_access_key_here"
secret_key = "your_secret_key_here"
- Validate that the configuration syntax for the prod workspace is correct:
$ terraform validate -var-file=prod.tfvars
- Apply the Terraform configuration to create resources in the prod environment:
$ terraform apply -var-file=prod.tfvars
You can create more variable files for different environments and apply them to their respective workspaces.
Note that each workspace will have its state file, so you can switch between them without affecting the resources in other workspaces. Make sure to switch to the correct workspace before running any Terraform commands to avoid making changes to the wrong environment.
Explore remote execution options such as using remote backends (e.g., AWS S3, Azure Storage Account, or HashiCorp Consul) and understand the benefits they offer.
Remote execution in Terraform allows you to run Terraform commands and operations using a remote source, such as Terraform Cloud or Terraform Enterprise, instead of running them locally on your machine.
When you use remote execution, your Terraform configurations (and modules) are stored on the remote source and executed remotely.
Using remote execution provides some benefits for teams, including:
Consistent environment: Because the Terraform commands are executed on an isolated environment set up by the remote source, you can ensure that each run is executed in the same environment, avoiding issues that might arise from differences in the local environment.
State management: When using remote execution, Terraform Cloud or Terraform Enterprise takes care of managing the state files, storing them securely and providing a way to share the state with other members of the team.
Collaboration: Remote execution makes it easier for multiple members of a team to work on the same infrastructure project. It provides visibility into what changes are being made when they are being made, and by whom.
Scalability: You can use remote execution when working on a large-scale infrastructure project. You can run the
applyanddestroyoperations remotely, which can be resource-intensive, and would not necessarily be feasible to execute locally.
To use remote execution, you will typically need to configure Terraform to use the remote backend by specifying the backend block in your Terraform code and providing the appropriate credentials. Once configured, you can use Terraform commands to initiate remote execution. Note that you will need to be authenticated and authorized to use a remote source such as Terraform Cloud or Terraform Enterprise.
Here's a step-by-step guide to using remote execution with Terraform Cloud:
Sign up for Terraform Cloud and create a new organization.
Create a workspace for your Terraform configuration.
Configure your Terraform code to use the remote backend. You can do this by adding a backend block in your configuration file, specifying the remote backend, and providing your Terraform Cloud API token. For example:
terraform {
backend "remote" {
organization = "my-organization"
workspaces {
name = "my-workspace"
}
}
}
Initialize your workspace by running terraform init. This will download any required provider plugins and set up the remote backend.
Write your Terraform code as you normally would, including whatever resources and modules you need.
Plan and apply your Terraform configuration by running terraform plan and terraform apply, respectively. These commands will execute remotely on Terraform Cloud. You will be prompted to confirm the changes before they are applied.
Check the status of your deployment by going to your workspace page in Terraform Cloud. You can see the state of the infrastructure, view logs, and see who made changes.
Once you are done with your environment, you can tear it down by running terraform destroy.
That's it! Terraform Cloud will take care of storing and managing the state file, so you don't have to worry about accidentally deleting it or losing it. Also, Terraform Cloud provides additional functionality such as version control integration, audit logging, and team management, which can make working with Terraform more collaborative and efficient.
Collaboration tools like HashiCorp Terraform Cloud or Terraform Enterprise
HashiCorp offers two main products for managing your infrastructure with Terraform - Terraform Cloud and Terraform Enterprise. HashiCorp Terraform Cloud and Terraform Enterprise are both enterprise-grade versions of Terraform, Terraform Cloud is a SaaS-based offering provided by HashiCorp, which provides teams with a central location for managing Terraform resources, as well as features like remote state management, version control integration, and collaboration workflows. With Terraform Cloud, teams can work together more efficiently, and it also provides an audit trail of all changes, making it easier to see who made what changes and when.
Terraform Enterprise, on the other hand, is a self-hosted version of Terraform that can be deployed in your own data center or cloud environment. With Terraform Enterprise, you can enjoy all the benefits of Terraform, combined with added enterprise features such as access control and policy enforcement. This makes it easier to manage large-scale Terraform deployments across multiple teams and environments.
Here's how you can get started with each one:
Terraform Cloud:
- Sign up for Terraform Cloud at https://app.terraform.io/signup/account. You can choose between a free or paid plan, depending on your needs.

- Create a new organization in Terraform Cloud. An organization is a workspace that you can use to store your Terraform configurations, state files, and other resources.

- Create a new workspace within your organization. A workspace is a logical environment where you can apply your Terraform configuration.

- Connect your workspace to a version control system (VCS) like GitHub or GitLab. Terraform Cloud will automatically monitor changes to your code and trigger runs whenever changes are detected.






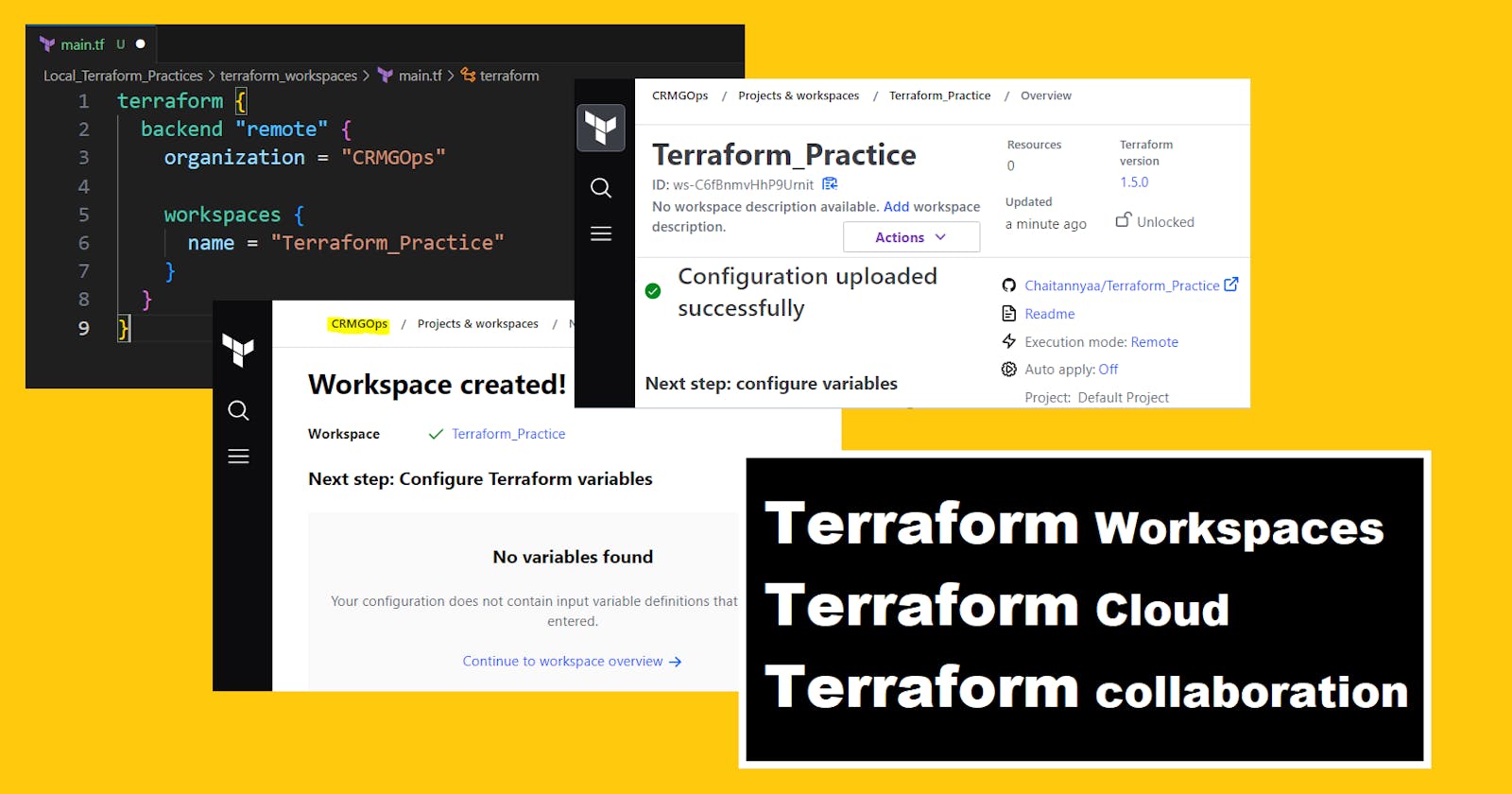
- Configure your Terraform code to use the remote backend. This involves adding a backend block in your configuration file, specifying the remote backend, and providing your Terraform Cloud API token. For example:
terraform {
backend "remote" {
organization = "CRMGOps"
workspaces {
name = "Terraform_Practice"
}
}
}
Initialize and apply your Terraform configuration by running
terraform initandterraform applylocally or by starting a run in Terraform Cloud. Terraform Cloud will automatically handle the plan, apply, and approval processes.Monitor the status of your deployment in the workspace page in Terraform Cloud. You can see the state of the infrastructure, view logs, and see who made changes.
Terraform Enterprise:
Install Terraform Enterprise on your infrastructure or use a hosted version.
Create a new organization within Terraform Enterprise.
Configure authentication for your organization, such as SSO with SAML.
Create a new workspace in your organization.
Configure your Terraform code to use the remote backend, similar to the steps above for Terraform Cloud.
Initialize and apply your Terraform configuration by running terraform init and terraform apply locally or by starting a run in Terraform Enterprise.
Monitor the status of your deployment on the workspace page in Terraform Enterprise. You can see the state of the infrastructure, view logs, and see who made changes.
Terraform Cloud and Terraform Enterprise offer similar functionality and workflows, but Terraform Enterprise allows you to host the platform on your infrastructure and customize it to better fit your needs.
What are the best practices for organizing your Terraform code, version control, and CI/CD integration?
Terraform's best practices include code organization, module usage, and naming conventions.
Terraform is a powerful tool for managing infrastructure as code, and some best practices can help you write efficient and maintainable Terraform code. Let's explore them:
Code Organization
Use a consistent directory structure for your Terraform code. Consider organizing it by resource types, cloud providers, or environments.
Break large configurations into smaller, more manageable modules. Each module should do one thing and do it well.
Use factored modules when possible, which are modules that have been broken down further into smaller components. This makes it much easier to reuse and combine modules in different ways.
Use version control for your Terraform code, ideally a Git repository. This enables collaboration, versioning, and change tracking.
Naming Conventions
Use descriptive names for all resources, variables, and modules. Avoid abbreviations and acronyms that may be unclear to others.
Use consistent naming across all your Terraform code. This makes it easier to search and understand your codebase.
Use a naming convention to identify the purpose of a resource. For example, a naming convention like env_role_app_resource can be used to identify the environment, role, and application of a resource.
Module Usage
Use modules provided by the Terraform community to save time and improve productivity. This reduces code duplication and makes it easier to create and maintain complex infrastructure.
Use module outputs to pass data between modules. This enables modules to be chained together and allows for easier customization and standardization.
Use remote state data sources to avoid duplicating state file information. This enables you to share data between different Terraform configurations.
Avoid hardcoding sensitive information into your Terraform code. Use input variables or secrets management tools like HashiCorp Vault.
These best practices should help you write maintainable, high-quality Terraform code that's easy to read, test, and scale.
Version control systems (e.g., Git) to effectively manage your Terraform codebase.
Version control systems like Git are essential for managing Terraform codebases, as they allow multiple team members to work on the same codebase simultaneously, track changes, and collaborate more effectively.
Here are the steps to effectively manage your Terraform codebase using Git:
Initialize Git in your Terraform project directory. Run
git initto create a new Git repository in your project directory.Create a
.gitignorefile and add all files/folders that should not be under version control. For example, you might ignore.terraform(where Terraform stores its files) andterraform.tfstate(where Terraform stores the state of your infrastructure).Create a new branch. It's a good practice to create a new branch for each new feature or change you make to the code. Run
git checkout -b <new-branch-name>to create a new branch and switch to it.Make the necessary changes to your Terraform code, such as adding resources or modifying existing ones.
Stage and commit your changes. Run
git add .to stage your changes andgit commit -m "commit message"to commit them.Push your changes to the remote repository. Run
git push origin <new-branch-name>to push your changes to the remote repository.Create a pull request (PR) for your changes. In your Git repository (on GitHub, GitLab, or another platform), create a new PR for your changes, and assign it to a teammate for review.
Review and merge the PR. After your teammates have reviewed your changes and suggested any necessary modifications, merge the PR into the main branch. This will trigger your CI/CD pipeline to apply the Terraform changes to your infrastructure.
By following these steps and using Git to manage your Terraform codebase, you can ensure that your infrastructure changes are tracked, reviewed, and applied consistently and securely.
How to integrate Terraform with CI/CD pipelines and implement automated testing, validation, and deployment strategies.
Integrating Terraform with CI/CD pipelines can significantly improve the speed and reliability of infrastructure changes. When Terraform code is integrated into a pipeline, it can be automatically tested, validated, and deployed, reducing the risk of errors and improving the overall quality of infrastructure changes.
Here are the general steps to integrate Terraform with a CI/CD pipeline:
Set up a version control system (VCS) repository to store your Terraform code. GitHub, GitLab, and Bitbucket are all popular VCS providers that work well with Terraform.
Write your Terraform code and store it in the VCS repository. Make sure to use best practices like modules, workspaces, and versioning to ensure that your code is reusable, easy to manage, and can be safely changed over time.
Set up a CI/CD pipeline. Popular CI/CD platforms that work well with Terraform include Jenkins, GitLab CI, Travis CI, and CircleCI.
Define a job in the pipeline to validate the Terraform code. You can use a linter or a tool like
terraform validateto check that your code is syntactically and semantically correct. For example, using a simple.gitlab-ci.ymlfile:
validate:
image: hashicorp/terraform:1.1.0
script:
- terraform init
- terraform validate
artifacts:
paths:
- .terraform
- Define a job to plan and apply changes. To prevent deployments that can cause issues, the changes must be tested before they are applied. Use
terraform planto quickly determine the changes that Terraform will make to the infrastructure and use variables files to test with different parameters. Additionally, definingterraform initto be sure the state file is in the correct backend. An example of how to do this usingJenkinsfile:
stage('terraform validate') {
steps {
container('terraform') {
sh 'terraform init'
sh 'terraform validate'
}
}
}
stage('terraform plan') {
steps {
container('terraform') {
sh 'terraform init'
sh("terraform plan -var-file=${params.tfvars} -out changes")
}
}
}
stage('terraform apply') {
steps {
container('terraform') {
sh 'terraform init'
sh 'terraform apply changes'
}
}
}
Define a job to store Terraform state safely. State management is a crucial aspect of Terraform and needs to be stored securely to avoid losing all your infrastructure's configuration. You should use a backend for storing the state (like S3, Azure Blob Storage, or HashiCorp Key/Value Store), and configure a remote state backend for
terraform(likes3for AWS), and ensure that the right Terraform version is used.Define a job to test the newly-deployed infrastructure. After applying the Terraform changes, you can test the infrastructure by running automated tests against the resources that have been created or updated.
Define a job to destroy the infrastructure. Remove the infrastructure created in the previous step by running the command
terraform destroy, using the same conditional and configuration files to guarantee the right components' deletion.
Features of Terraform Cloud, Terraform Enterprise, and Terraform Registry
Terraform Cloud or Terraform Enterprise provides enhanced collaboration, infrastructure management, and workflow automation capabilities.
Terraform Cloud and Terraform Enterprise feature related to collaboration, infrastructure management, and workflow automation:
Collaboration:
Remote State Management: Both Terraform Cloud and Terraform Enterprise offer centralized storage for Terraform state files. This allows multiple team members to work on the same infrastructure code simultaneously, ensuring consistent and synchronized infrastructure deployments.
Version Control Integration: Integration with popular version control systems like Git enables versioning and tracking of changes to infrastructure code. It facilitates collaboration, code reviews, and easy rollbacks.
Collaborative Workspaces: Workspaces in both platforms allow teams to separate and manage different infrastructure environments (e.g., development, staging, production). This segregation helps maintain isolation and clarity in managing infrastructure configurations.
Infrastructure Management:
Policy Enforcement: Terraform Cloud and Terraform Enterprise provide policy enforcement capabilities to define and enforce compliance rules, best practices, and security standards across infrastructure code. This ensures adherence to organizational standards and reduces the risk of misconfigurations.
Resource Management: Both platforms offer features to track and manage infrastructure resources provisioned through Terraform. This includes visibility into resource dependencies, changes, and status tracking, providing insights into the overall infrastructure state.
Module Management: Terraform Cloud and Terraform Enterprise support the use of modules, which are reusable components that encapsulate infrastructure configurations. They facilitate modular and scalable infrastructure design, code reuse, and maintainability.
Workflow Automation:
Run Automation: Terraform Cloud and Terraform Enterprise enable automation of Terraform runs, including plan and apply operations. This allows for scheduled or triggered runs based on events (e.g., code commits, infrastructure triggers), reducing manual effort and streamlining the deployment process.
API and CLI Access: Both platforms offer APIs and command-line interfaces (CLIs) that allow for programmatic access and integration with external systems. This enables custom workflow automation, integration with CI/CD pipelines, and automation of common infrastructure tasks.
It's important to note that while Terraform Cloud is a SaaS platform provided by HashiCorp, Terraform Enterprise is the self-hosted, on-premises version. They share many similar features but differ in terms of deployment options, control, and security based on your organization's requirements.
Terraform Registry and explore its vast collection of modules and providers to extend the functionality of your infrastructure code.
The Terraform Registry is a central repository of Terraform modules and providers that allows you to extend the functionality of your infrastructure code. It provides a wide range of pre-built, reusable modules and providers created by both the Terraform community and official providers.
Explore the Terraform Registry:
- Accessing the Terraform Registry: You can access the Terraform Registry at registry.terraform.io. It provides a user-friendly interface to search and browse available modules and providers.
Terraform providers 3272 providers are available.
Terraform modules 13746 modules are available.
When using modules and providers from the Terraform Registry, it's important to review their documentation, check their popularity, and ensure they meet your specific requirements. Additionally, be mindful of any version constraints or compatibility considerations with your existing infrastructure code.
Happy Terraforming! 🌍💻
Keep exploring and experimenting with Terraform to build your infrastructure on multi-cloud platforms. Happy learning! 😊
#TrainWithShubham #TerraWeek Challenge
I hope you learned something today with me!

Stay tuned for my next blog on "Monitoring tools for DevOps". I will keep sharing my learnings and knowledge here with you.
Let's learn together! I appreciate any comments or suggestions you may have to improve my learning and blog content.
Thank you,
Chaitannyaa Gaikwad