Terraform Configuration files, State files, Resources and lifecycle Management
TerraWeek Day 3/7
Task 1:
Create a Terraform configuration file to define a resource of AWS EC2 instance, Azure storage account, Google Compute Engine, etc. (anyone)
AWS EC2 instance--->
terraform init
Similarly for Microsoft Azure and Google Cloud providers
Azure storage account--->
Google Compute Engine--->
Task 2:
Check state files before running the plan and apply commands & Use validate command to validate your tf file for errors and provide the Output generated by each command.
Check my state file here---> terraform.tfstate
AWS EC2 instance--->
terraform plan
terraform validate
Task 3:
Add a provisioner to the configuration file to configure the resource after it is created and use Terraform commands to apply for changes and destroy to remove resources.
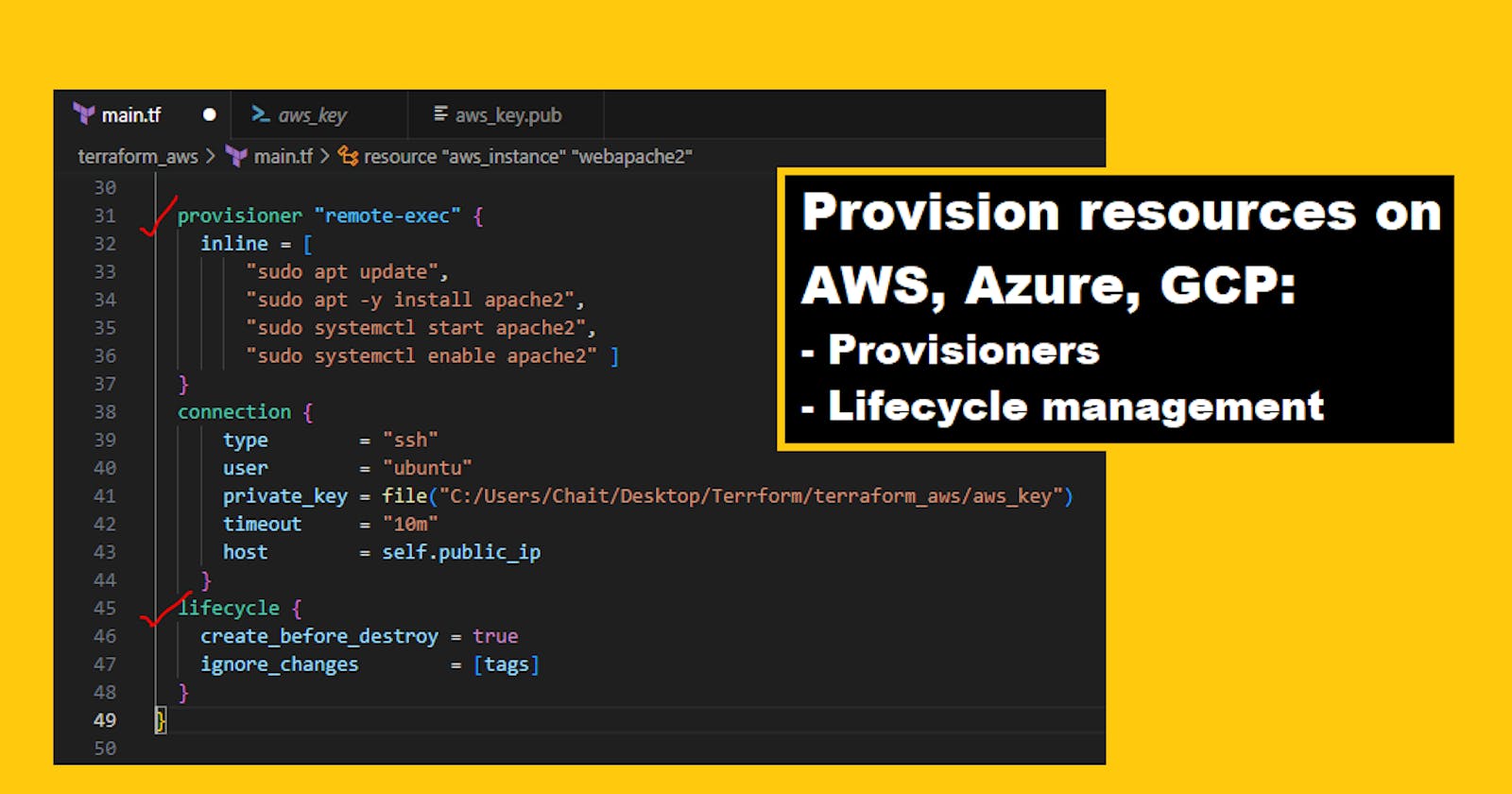
What is provisioner in terraform--->
In Terraform, a provisioner is a configuration block that defines how to perform actions on the resource after it has been created, updated or deleted. Provisioners can be used to install packages, run scripts or perform any other kind of post-creation or post-update configuration.
Provisioners are especially useful when you need to perform actions that are not included in the provider’s functionality, such as customizing the software installed in your instances or applying a custom configuration.
There are different types of provisioners supported by Terraform, including:
local-exec: runs a command on the machine running Terraform
remote-exec: runs a command on the remote machine through SSH
Chef: applies a Chef role or cookbook to a node
ansible: applies an Ansible playbook to a node
Provisioners are defined within the resource block and can be triggered on create, update, or delete operations. The local-exec and remote-exec provisioners are available with all providers, while the chef and ansible provisioners are specific to the corresponding providers.
Let's use provisioner--->
terraform init
terraform apply
Task 4:
Add lifecycle management configurations to the configuration file to control the creation, modification, and deletion of the resource and use Terraform commands to apply the changes.
Terraform lifecycle management configurations are used to control the creation, modification, and deletion of resources in your infrastructure. Lifecycle management configurations help you manage the behavior of your infrastructure over time, by specifying how Terraform should handle updates and destructions for certain resources.
Here are some of the common scenarios where lifecycle configurations might be useful:
When you want to replace an instance with a new one, you want to avoid downtime. In this case, you can create the new instance before destroying the old one, by setting create_before_destroy flag to true. When you want to disable resource deletion, to avoid accidental deletion of important resources. In this case, you can set prevent_destroy flag to true. When you want to update a resource only under certain conditions. In this case, you can set prevent_resource_replacement to true and specify the conditions for the update.
Here's an example of the lifecycle configuration block syntax:
resource "my_resource" "example" {
# resource configuration
lifecycle {
create_before_destroy = true|false
prevent_destroy = true|false
ignore_changes = [ attribute_name, ... ]
prevent_replacement = true|false
}
}
Here's what each parameter does:
create_before_destroy: This parameter is used to control whether the resource is created before destroying the old one. If set to true, Terraform will create the new resource before destroying the old one. This can help prevent downtime during updates.
prevent_destroy: This parameter is used to control whether the resource can be destroyed. If set to true, Terraform will not be able to destroy the resource, even if you try to force it. This can help prevent the accidental deletion of important resources.
ignore_changes: This parameter is used to specify attributes that should be ignored when Terraform calculates if the resource should be updated or not. This can help prevent certain attributes from being updated under certain conditions.
prevent_replacement: This parameter is used to control whether the resource should be replaced when it's updated. If set to true, Terraform will try to update the resource in place, without replacing it.
Let's use it in our configuration--->
I will change my web server from Nginx to Apache2
terraform apply
This is how our new instance is provisioned and then the first one was terminated
(Lifecycle management _Create before destroying the existing one).
Happy Learning :)
#TrainWithShubham #TerraWeek Challenge
I hope you learned something today with me!

Stay tuned for my next blog on "Day4 of Terraweek Challenge". I will keep sharing my learnings and knowledge here with you.
Let's learn together! I appreciate any comments or suggestions you may have to improve my learning and blog content.
Thank you,
Chaitannyaa Gaikwad